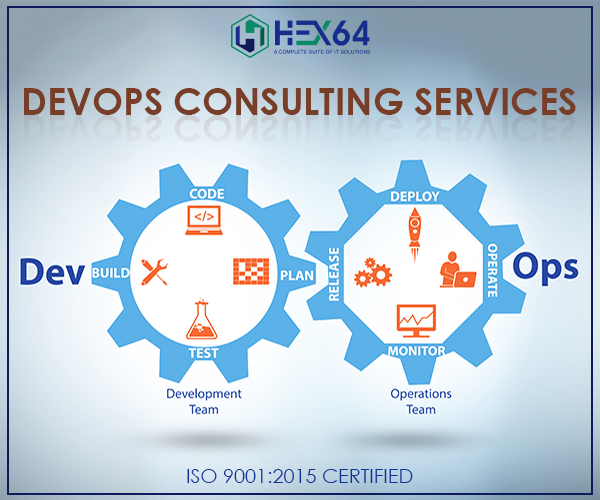
Today, businesses have to execute the project ASAP to be one step ahead of the competition, but it usually happens that businesses have limited funds. There has been a connection between the deployment of DevOp...
The labels and terminology we use are essential in highly technical areas such as IT service management. We need clear, commonly held definitions in order to communicate and collaborate effectively. With...
Have you ever wondered why you want an IT consultant for your enterprise? How can hiring these experts to be a big advantage?If not yet, it’s time to stop focusing on the bigger picture and focus on your ...
Businesses that understand how to prevent a data breach can incur costly penalties, loss of business and destroy their reputation. With more and more collaboration between companies, merchants, suppliers and us...
The world of software development underwent a major change with the emergence of DevOps in 2008. This led to a fundamental shift in focus in the company’s culture, organizational principles, and approach ...
Penetration testing is an effective testing process that helps to uncover the critical security issues of your system to check for exploitable vulnerabilities to their IT Infrastructure, or web applications. ...
Static server room infrastructure will soon be an IT residue. Digitization has accelerated innovation in business infrastructure, heading to the division of devices and applications beyond the IT ecosystem. Whi...
Pegasus is spyware produced by NSO Group, it’s an Israeli surveillance company, that helps spies and spies hack phones. In 2019, the situation came to light when WhatsApp charged the business in a US cour...
Now that the modern workplace becomes more and more sophisticated as it is interconnected, businesses should expect more complex and targeted attacks that threaten an organization’s entire infrastructure ...
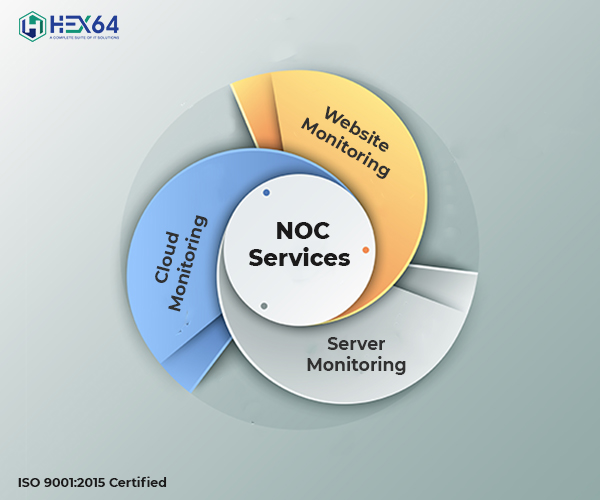
Network operations deal with the activities executed by internal networking teams or third parties that organizations and service providers rely on manage, monitor and respond to alerts on the administration an...