With the increasing reliance on technology, it is becoming increasingly necessary to secure every aspect of online information and data. As the Internet grows and computer networks become more important, data i...
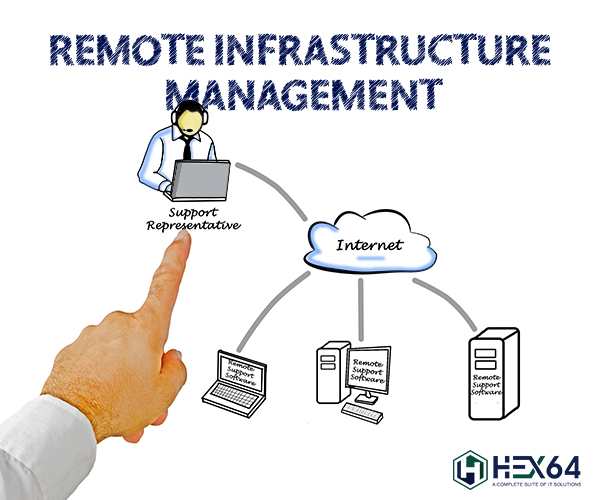
What is RMM (Remote Monitoring And Management)? In essence, it is the method of controlling SMB IT systems such as desktops, laptops, and servers that are on the network and these devices can be managed through...
With the improvement in technologies and change in customer demand, the idea of business expansion has changed. Companies are taking steps to intensify their enterprise practices to meet changing customer requi...
A cybersecurity audit is planned to comprehensively analyze and study your company’s IT infrastructure. It identifies threats and vulnerabilities that highlight vulnerable locations and high-risk performa...
Assume all the problems you face when you try to connect to a network. You may have seen cases where you are making everything right but still helpless to connect. Let’s take another example where ...