Network management is a multifaceted control that needs a cohesive attempt to provision, protected, optimize and maintain efficient enterprise operations. This begins with getting everything the factors that co...
Remote Infrastructure Management is a method of managing the IT infrastructure of a business from a remote location. It combines the management of devices like Server, Firewall and software, network and storage...
In this blog, we will solve the problem that prevents the user from logging into the Dell EMC Data Domain System Manager Graphical User Interface from a web browser. Issue- When User is trying to launch Data Do...
If an SA password is ever lost then instead of re-installing SQL and re-attaching the DB, SQL Server provides a great disaster recovery method that keeps objects and data in the master DB. Members of the server...
Absence of penetration testing, a fresh study found that 33% of enterprises have dropped customers because of a breach. Not just will this variety of security events more add to the prices of the potential dama...
From Veritas Backup Exec 2014 onwards, it has no option to delete the backup sets however we can set the expiry date to clean up backup sets. In this blog we are showing how to remove backup set in Veritas Bac...
In this blog we are showing if you are getting error while getting error the server is unreachable how to resolve the issue. Issue– 1. On a 64-bit system, you install an instance of the 32-bit version of ...
In this blog we are showing how to free upgrade Windows 7 to Windows 10. System Requirement – 1. Processor – 1 GHz or faster processor. 2. Memory – 1 GB for 32-bit OS or 2 GB for 64-bit OS. 3. Hard ...
Enable Continuous Delivery Pipeline Across Cloud Platforms for Increased Efficiency and Reduced Cost
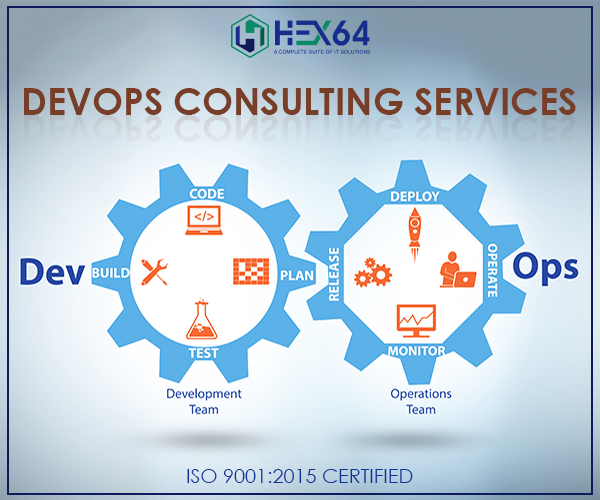
What is DevOps? DevOps is the conjunction of traditional sight, exercises, and tools that growth a company’s ability to produce applications and services at huge quickness: growing and promoting products at a q...
The various-cloud network is a cloud network that consists of larger than individual cloud services provider. A sincere type of various-cloud network includes multiple infrastructures as a service (IaaS) mercha...